
Layered Protection for Data at Rest
Ensure data on edge devices is protected and meet CSfC for DAR requirements
Data at rest on edge devices is vulnerable to unauthorized access potentially revealing critical sensitive data. NSA's Commercial Solutions for Classified (CSfC) program sets stringent requirements requiring layered protections. Cigent provides SSDs and software to ensure data at rest is protected and enables organization to meet CSfC DAR requirements.

Proven Solution
Cigent provides hardware and software capabilities to protect data at rest and meet CSfC DAR compliance requirements. The joint solution has been rigorously tested and validated by NSA and NIAP and other certifying organizations. Alternatively, you can also utilize SSDs through our strategic partner, Digistor, which has undergone rigorous testing and joint development.

Enterprise Management
Cigent utilizes a Command Line Interface (CLI) tool that seamlessly integrates within existing management to provide enterprise administration. CLI operates with both Linux and Windows environments.

Data Sanitization
Cigent utilized and crypto and block erase to sanitize data. In addition, Cigent provides a patented verification that confirms at firmware level that each data block has been erased. This is the only way to ensure all data has been successfully destroyed.

Streamline Acquisition
Cigent SSDs and Software are available directly from leading device manufacturers directly within their configuration process simplifying acquisition process. Device OEM partnerships include Dell, HP, GETAC, and Panasonic.
.png?width=2000&name=Layout%201%20(1).png)
Cigent Protection
Understanding CSfC for DAR Protection
Includes Hardware Full Drive Encryption with PBA. This is the outer layer as it provides the initial protection layer. It includes:
AES-256 Hardware Full Drive Encryption
Utilizing NSA-validated cryptography. Encryption keys are not stored in TPM or in aggregate preventing interception or compromise.
Pre-boot Authentication (PBA)
Providing a separate, secure environment to unlock drive encryption. The approach prevents an adversary from compromising the OS-boot to access.
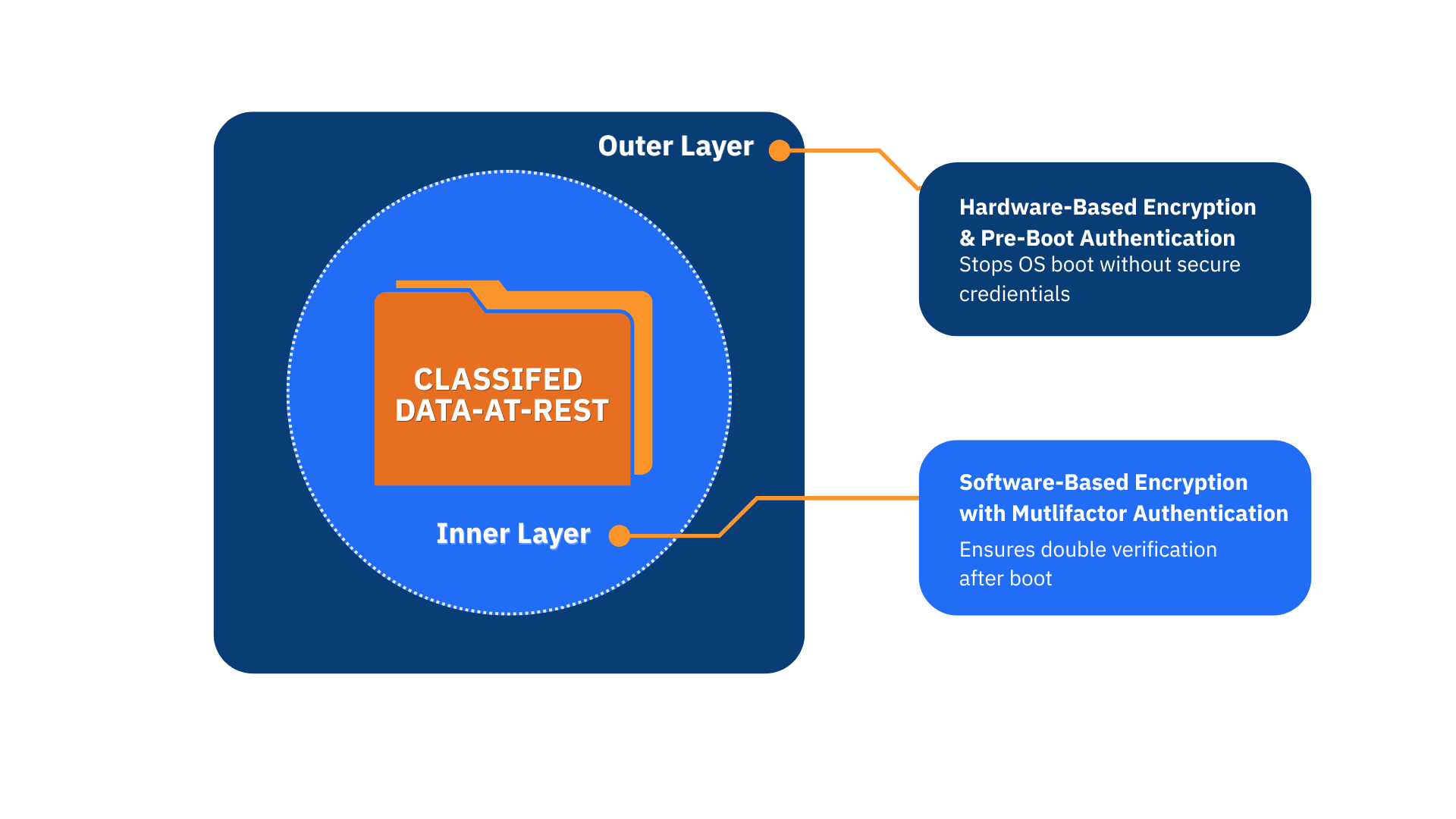
Includes Software Full Drive Encryption with multifactor authentication (MFA). This is the inner layer as it provides protection after the outer layer has been unlocked. It includes:
AES-256 Software Full Drive Encryption
AES-256 Software Full Drive Encryption utilizing NSA-validated cryptography. Software encryption employing pre-OS boot.
Multifactor Authentication
MFA prevents an adversary from unauthorized access through the compromise of a single credential. MFA requires use of both U/N Password and smart card (CAC) or security key.

Coverage
Protection for devices operating at the edge.
Personal Computers
M.2 2280 and M.2 2230 SSDs
with Hardware Full Drive Encryption
Pre-boot Authentication software
Software Full Drive Encryption
Linux and Windows O/S
Workstations & Servers
U.2 Enterprise Storage SSDs with Hardware Full Drive Encryption
M.2 2280 SSD Boot Drive
Boot drive is a storage device that contains the files needed to start the operating system.
SATA/NVMe available through Digistor
Pre-boot Authentication software
Linux and Windows O/S
The Cigent Advantage
Cigent solutions were designed and developed with and for US Intelligence and Defense communities. All employees, including Cigent software development, are based in the US. The team includes multiple personnel with TS/SCI clearance with decades of data protection and operational experience to support your requirements.
Cigent solutions have been tested and validated by leading Federal agencies including MITRE, NIST, NSA, NIAP, the Air Force, Cyber Resilience of Weapon Systems (CROWS), and NSSIF (UK) and are deployed across US Intelligence agencies, US Defense services, and the defense industrial base.

ebook
Protect Your Data at Rest
Cigent is prepared to support your mission navigating the complex compliance requirements to protect data at the edge. Its solutions were developed for and with US Federal agencies with deep expertise in data protection. Read our extensive eBook to learn more.


provide value to the visitor
Cigent PBA 2.0 Achieves NIAP Listing and CC Certification, Advancing Pre-Boot Authentication for CSfC DAR Protection
New Executive Leadership and Purpose-Built Software Drive Growing Demand for Secure ..

Strengthening Data at Rest Protections: Lessons from Recent Espionage Cases
Strengthening Data at Rest Protections: Lessons from Recent Espionage Cases

Cigent Announces New CEO and Introduces Software Full Drive Encryption Designed for CSfC Compliance
New Executive Leadership and Purpose-Built Software Drive Growing Demand for Secure ..
Frequently Asked Questions
Check out the answers to some of most frequently asked questions about Cigent, what we do, and how we do it. Don’t see your question on the list? Click the BOOK A DEMO button in the top right corner of your screen to learn more about us during a custom demo.
Cigent protects data on devices operating at the edge from unauthorized access. Cigent solutions secures data at rest with layered protection including hardware encryption, pre-boot authentication, and multifactor authentication. Cigent also ensures data integrity when the device is in use preventing wiping and cloning and other data attacks.
To prevent sophisticated adversaries from unauthorized access requires layered protection. The foundation of Cigent solution is 256-AES full drive hardware encryption with pre-boot and multifactor authentication. These capabilities have been validated by agencies including NSA and NIAP. Additionally, Cigent provides capabilities that ensure the integrity of data through its lifecycle including hidden partitions, storage-embedded AI, and verified data erasure.
Data at rest encryption traditionally refers to the encryption of data when the device is asleep or powered-off. Data at rest encryption seeks to prevent adversaries who gain physical access to the device would seek to extract sensitive data. Cigent uses AES 256 full drive hardware encryption with pre-boot and multifactor authentication. In addition, Cigent uses zero-trust access to control to also protect data when a device is in use. This is with hidden partitions that maintain encryption until it is accessed with step-up authentication.
Pre-boot authentication (PBA), also known as power-on authentication, is a security feature that requires users to authenticate before their device boots up. PBA is a layered approach that protects devices and data from offline attacks and cyberattacks. It's often used with full disk encryption (FDE), where users must authenticate to boot the system and restore data. Cigent PBA has been tested and validated by leading organizations including NSA, DISA, NIST, and NIAP.
Cigent provides the widest breadth of secure storage solutions all utilizing hardware encryption. These includes: PCs supporting both M.2 2280 and the emerging M.2 2230 standard, remote servers and NAS devices with U.2 drives, external media with flash drives, encrypted external drives, SD and Micro SD cards, and embedded for SSD BGA.
Yes, Cigent Secure Storage Solutions can support organizations meeting Commercial Solutions for Classified (CSfC) for data at rest including pre-boot authentication requirements. Cigent solutions can also meet FIPS 140-2 and 140-3 standards. Additionally, Cigent can address requirements from Executive Order 14028 including encryption of data at rest, multi-factor authentication, and the utilization of zero-trust access control. Cigent protections have been thoroughly tested and validated by leading Federal agencies including MITRE, NIST, NSA, NIAP, the Air Force, Cyber Resilience of Weapon Systems (CROWS), and NSSIF (UK).
Still have questions?
Learn more about Cigent and our solutions by downloading our company overview.

Cigent’s Federal Data Protection Solutions are second to none
Learn more about how Cigent can help you achieve your mission and protect data at rest and data on the edge from all forms of attack.
© 2025 Cigent Technology Inc.




